How is access to the network controlled and, especially, is there a piece of equipment to do that? These are the questions we will answer in this video. We must remember that it’s not just data packets corresponding to the video stream I’m watching that are travelling on the network. There’s also a set of control functions to be put into place. We will, for example, verify that the subscriber is authorized to use the network before giving him access.
The HSS, Subscriber Database
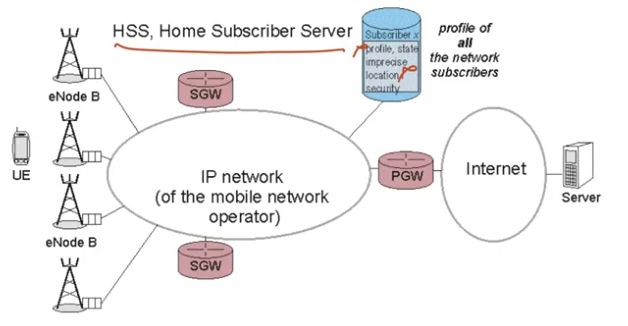
If he is not authorized because he did not pay his bill, for instance, the access should be refused. These control procedures require the use of a database. In 4G, this is called the HSS, Home Subscriber Server. It was called the HLR (Home Location Register) in 2G/3G. In the HSS, we find the profile of all the network subscribers, that is, the list of all the subscribers, their identity, their rights, I mean the services subscribed to, and their location.
There are also security data, which enable access control. The location of the subscriber is very imprecise. We’ll look at these elements in other posts.
To check the profile of a subscriber or get an idea of his location, we need signaling. What is signaling? Signaling is the set of messages exchanged to manage network access. Signaling does not contain user data, what I mean is, it’s not the video stream or the content of a web page.
It is control information that is useful for the operator. Signaling corresponds, for example, to access control, to the tracking of terminals when they move. The HSS, this is a very important point, only exchanges signaling. It only takes care of control: no data packet corresponding to the video stream, to continue my example, goes through the HSS.
Throughout this course, we will present elements specific to control in blue. So, if I try to access the network of an operator other than mine, when I try to access this network, the terminal will send a message that will be forwarded up to the HSS and it will verify the access. If I’m not on the subscriber list, I will be refused access.
If we analyze a bit what can happen, we have several tens of millions of subscribers in the network. That corresponds more or less to several tens of millions of terminals.
MME, Mobility Management Entity

If, every time someone moves or does something on his terminal, and we want to control access, we have to send a request to the HSS. The HSS, even though they are powerful, risk being saturated, having to manage this set of simultaneous control requests. On top of that a lot of signaling exchanges to manage the sporadic we need nature of transmissions. we’ll see this in the course.
Therefore, we introduce the MME, the Mobility Management Entity. The MME manages a very large region and will be connected via the operator’s network to various eNodeBs. The objective of the MME is to control mobility, to control the various terminals. This means that, when I turn my terminal on, it sends a request to the eNodeB which will send a request to the MME at the moment of what we call ‘attachment’ to the network and then the MME checks to see if it knows the subscriber. Generally, he’s not known if this is the first time the terminal is powered up.
So, the HSS will transmit to the MME the subscriber profile, that is, all his access rights, the services he’s subscribed to. Then, for all future access, each time there’s a verification to make, the MME will be able to verify locally the subscriber profile recopied in the MME. It’s the equivalent, in a way, to cache memory for programmers. So, the MME is the node that will be, in a way, the local or regional conductor. There are several MMEs in a national French network.
Principle Functions of the MME
Like HSS, the MME only exchanges signaling. MMEs are relatively powerful machines that can manage around ten million subscribers. We list the main functions of the MME. The MME communicates with the various base stations to establish, for example, configuration functions. It also communicates with the HSS to get the profiles and security information of the subscribers present in the zone it manages.
The MME stores these profiles and security data. It manages the control mechanisms related to network access, security and mobility for terminals present in its zone. It also maintains an awareness of the location of the terminals in its area, but in a relatively imprecise way. It selects the P-Gateway and the S-Gateway when the terminal attaches to the network and connects to the Internet.