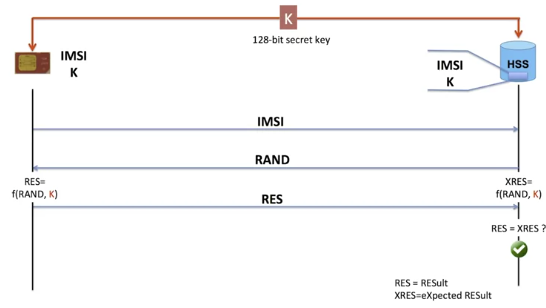
Each subscription is identified by an IMSI, which is unique in the world.
For each subscription, there is also a secret key K. This key is stored both in the SIM and the HSS.
The key is 128 bits long, which gives 3 10^38 possible values, more than the number of grains of sand on the earth !
Practically, there is no chance to have two SIMs with the same key.
When the UE attaches to the network, it sends its IMSI. To authenticate the subscriber, the network checks the presence of the secret key in the SIM card without ever transmitting this key on the radio channel.
The method is based on a cryptographic function and a challenge. This challenge is simply a random number RAND coded on a large number of bits.
Both the HSS and the SIM card make a calculation using the same cryptographic function called f on the figure. The f function takes as input the random number RAND and K, the secret key, and gives a result. The terminal calculates the result and sends it to the HSS.
The HSS compares RES to the expected result. That is, the XRES calculated.
If RES equals XRES, then it’s interpreted as proof that the mobile terminal is in possession of the shared secret.
So, if it really is the subscriber the UE claims it is, the UE is authorized to communicate with the mobile network.
If there is a difference between RES and XRES, the UE is refused network access. The cryptographic function was specifically chosen because it’s simple to calculate, using the RAND and the key.
In 4G, the random number RAND and the key are 128 bits. The result of the function is a number from 32 to 128 bits. Knowing the random number and the result will not enable you to determine the value of the key. This is a one-way algorithm. If someone is listening to the values RAND and RES, he cannot deduce the value of the key. When a subscriber is abroad, it’s still the HSS that generates the random number and determines the XRES.
Both ends of the chain, the HSS and the SIM are completely under the control of the operator. Each operator can define his own cryptographic function completely autonomously, as long as the sizes of the challenge and of the result conform to specifications. Note that a trusted third-party can play the role of authenticator.
The HSS just needs to provide the random number RAND and the expected result XRES. It’s the third party’s responsibility to verify the correspondence.
In truth; the terminal never interacts directly with the HSS. It’s the MME that plays the role of authenticator. The terminal initiates the procedure by sending the IMSI to the MME via the eNodeB.
The MME contacts the HSS. The HSS generates the random number RAND to pass to the terminal and the expected result XRES. The HSS sends these elements to the MME. The MME sends the random number RAND to the terminal via the eNodeB and waits for the response.
If the terminal’s result corresponds to the expected response XRES, the MME authorizes the terminal to enter the network.
The RAND-XRES pair constitutes the base of what we call an authentication vector. The vector contains several other elements that we’ll see later.
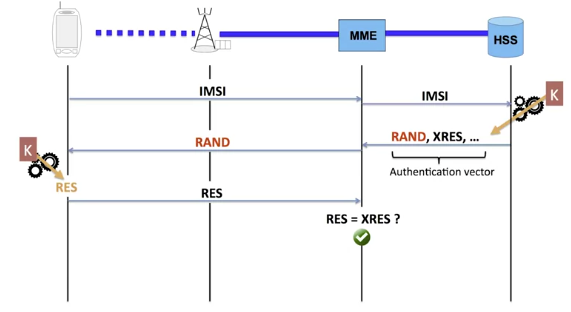
Of course, once the vector has been used, we can’t use it a second time.
We’ve seen how the network authenticates the terminal. Nothing prevents an attacker from making up a fake base station and passing itself off as a real network. With the procedure we’ve seen, the terminal has no proof that the challenge it received and that the response it sent weren’t processed by a pirate network. That’s why, in 4G networks, there’s mutual authentication. That is, the network authenticates the terminal and the terminal authenticates the network.
Let’s look at how it works.
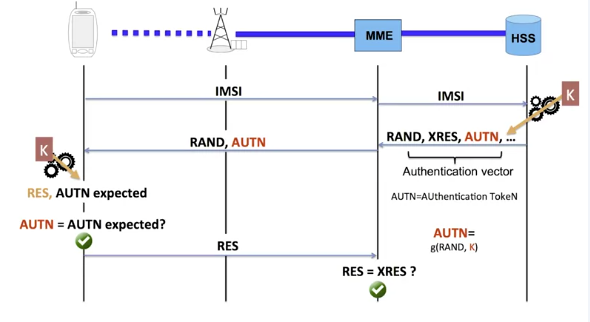
We’re still using the random number, a cryptographic algorithm g, and calculating a result that is called, in this case, an authentication token, or AUTN. The authentication algorithm of the network g is different from the authentication algorithm of terminal f.
The token AUTN is therefore different from the result RES. The HSS transmits the token as well as the random number.
The MME sends in the same message the random number RAND and the authentication token AUTN to the terminal. The terminal does its own calculations and verifies that it got the same value as the received token.
If this is the case, the network is authenticated by the terminal and exchanges continue as we saw previously.
If we applied this procedure exactly, there would be a major weakness. An attacker can just listen to the network and note the RAND and the corresponding AUTN token.
He then takes over the role of the network and sends the RAND-AUTN pair he has noted. Therefore, two successive authentications must lead to different results. So, we introduce a new input parameter called SQN for Sequence Number.
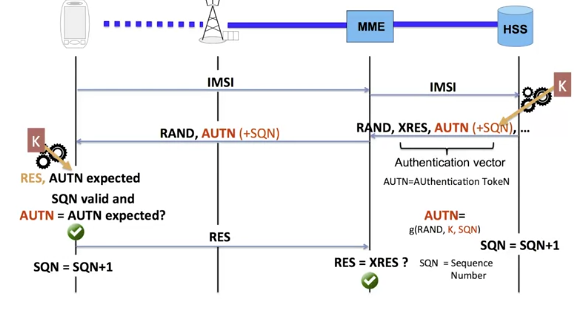
The basic principle is to increment the value of SQN with each new authentication. A part of the authentication token, AUTN contains information about the SQN number.
So, when receiving the authentication token, the terminal verifies that the SQN does not have the same value as the last time, in other words that the SQN is valid.
If the SQN Is not valid or if the authentication token is not the expected one, the terminal does not access the network. If everything is OK, the terminal computes the RES value and sends it to the MME.
The MME checks that RES is the same as XRES. After these exchanges, the terminal and the network are mutually authenticated. The terminal can use the network.
Of course, SQN should be incremented. A new authentication vector will have the new SQN value. The use of authentication vectors is important because it enables a large flexibility in the authentication mechanism and in the network.
So, the HSS never communicates with the mobile terminal. It just receives an authentication request and responds with authentication vectors.
All the protocol exchanges between the MME and the mobile terminal are hidden from the HSS and do not concern it.
Another important point is the management of roaming situations. A foreign MME can ask the HSS for authentication vectors.
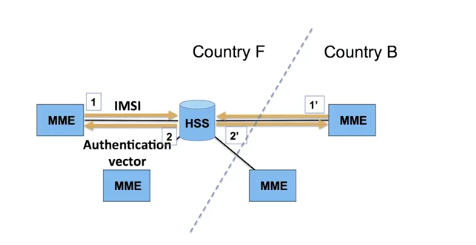
Without having access to the secret K, the MME will then be able to authenticate the mobile terminal.
Authentication Summary
- Based on a secret key, cryptographic functions and random numbers
- The secret key is stored in the SIM and the HSS
- The secret key is never transmitted in the network
- The SIM and the HSS make the same calculation.
- The authentication is valid when both find the same results
- Mutual Authentication
- Authentication of the UE by the network
- Authentication of the network by the terminal
In summary, in 4G networks, authentication is based on a secret key, cryptographic functions and random numbers. The secret key is stored in the SIM and the HSS. The secret key is never transmitted in the network. The SIM and the HSS make the same calculation. The authentication is valid only when both find the same results. The authentication is mutual: the UE authenticates the network and the network authenticates the terminal.