Of course, the answer is NO. We’re going to see the security mechanism put in place to guarantee the confidentiality of exchanges. Especially ciphering, which is also called encryption.
In networks, ciphering is based on a very simple mathematical operation which is XOR, in other words the exclusive OR between the clear text and a sequence generated by the sender.
This operation works bit by bit so it takes one bit from every sequence and produces a bit as output. If the two bits are the same, the result is zero. For example as shown in the slide, 1 XOR 1 equals 0.
The operation is very simple to implement in hardware. In this example, the clear text is in blue and the ciphering sequence is in red.
It should be noted that the sequence must have the same length in bits as the input data.
To get the clear text from the ciphered data in green, you just need to repeat the operation with the ciphering sequence.
There is one big constraint: the ciphering sequence must be different every time.
If we use the same sequence several times, we completely lose all security properties.
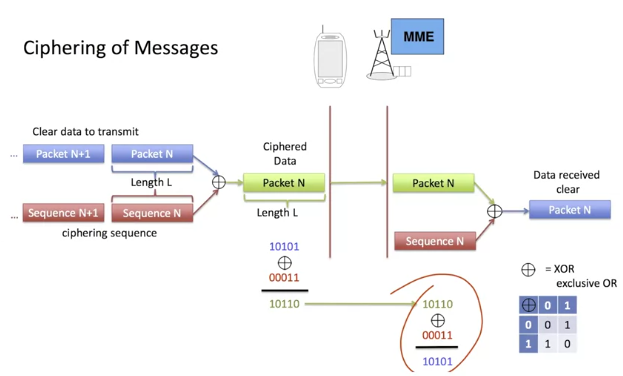
When we have a very large volume of data to transmit, we’ll cut it into various packets and we’ll try to cipher the packets with different sequences.
The receiver must possess the same ciphering sequence in order to be able to get the clear text. But how can we obtain a ciphering sequence of an almost unlimited size?
We use an algorithm that, based on a few input parameters, generates sequences adapted to the data ciphering. We start with a basic ciphering key that is relatively stable.
It is conserved, for example, throughout a Web session or during an entire communication. This shared key Kenc is the basis for creating an almost unlimited number of ciphering sequences.
The ciphering key is calculated from the number RAND used for authentication and from the secret K.
It is essential to use specialized functions that ensure that the string of sequences produced is the closest possible to random values.
Because these are deterministic algorithms, if all input parameters are the same, the function will produce the same ciphering sequence as output. Therefore, we’ll try to add elements known only by the sender and the receiver which change with all new data sent.
For example, we’ll number each transmitted packet and integrate the packet number and the amount of data to cipher in the input parameter of the algorithm used to calculate the ciphering sequence.
We’ll also place a direction indicator (uplink or downlink) and a bearer number. We’ll take a look at bearers in chapter 4. At this point of the course, we can see it as a stream.
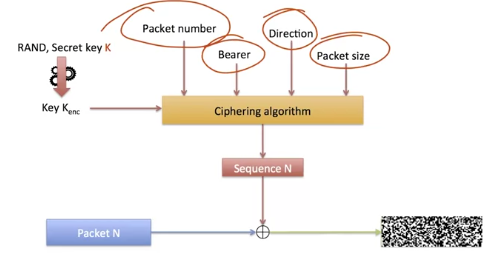
The ciphering algorithm is executed on the mobile terminal and on the eNodeB. The algorithm used must be standardized: an operator cannot define his own ciphering algorithm.
All radio transmissions are ciphered, whether they are user data or signaling. Moreover, data exchanged between the MME and the mobile terminal are ciphered by both sides.
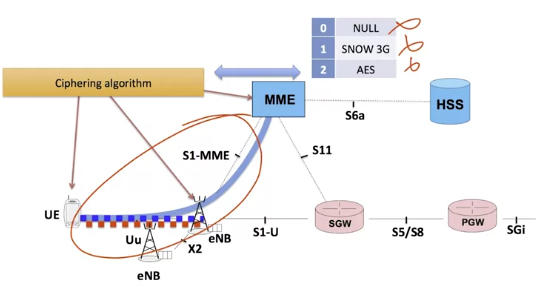
As for ciphering algorithms, there are several. Here, you see the three that are currently standardized in the LTE network. The first, NULL, which does not cipher data is to be prohibited and only used during network test periods. The second, SNOW 3G, is an algorithm present in third generation networks and the AES which gives the strongest security guarantees at this moment.
Each of the exchange channels illustrated here can use a different ciphering algorithm. The ciphering algorithms and the ciphering keys are negotiated during the terminal authentication phase.
Now here is an example to illustrate the different ciphering stages for an IP packet which contains user data coming from the Internet.
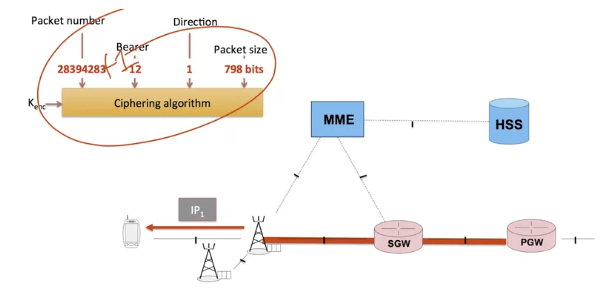
Let’s consider a packet arriving at the P-Gateway which is then routed across the core network where its confidentiality is guaranteed by the classic mechanisms of the Internet world before arriving at the eNodeB.
The eNodeB cyphers this packet before sending it on the radio link. We can imagine that the following values are used to generate the key used to encrypt the frame: number of the packet counter between the eNodeB and the terminal, reference of the bearer, downlink or uplink packet, and size of the data to encrypt.
The ciphering key negotiated earlier between the mobile terminal and the eNodeB during the authentication phase must also be specified.
Upon reception, the mobile terminal uses the same parameters to decrypt the frame. The next IP packet will follow the same path, but in this case the frame counter will increment by 1 and so, even if it uses the same shared secret, a completely new ciphering sequence will be used.
Summary
- Based on stable encryption key
Kencgenerated with secret key K and the random number used during authentication - Ciphering sequence specific to each packet generated with
Kencand parameters including a packet counter - Ciphering based on XOR
- Ciphering and De-ciphering are the same operator
In summary, Ciphering also called encryption is based on a stable encryption key Kenc generated with secret key K and the random number used during authentication.
The ciphering sequence is specific to each packet. It is generated with Kenc and parameters including a packet counter. Ciphering is based on XOR (exclusive Or). Ciphering and De-ciphering are the same operation.